Does Cyber Security Have to Be a Stumbling Block?
A few years ago, almost half of business leaders polled said that they hadn’t invested in cyber security in the last year. Given the obvious importance of staving off data breaches, phishing scams, business email compromise, and the like, this gap is a little bit shocking. And yet, even today more than half of businesses say that they don’t have the resources or the knowledge to develop a robust cyber security strategy. As such, the specter of InfoSec looms above businesses that don’t necessarily have a handle on what it means—they think of it as an onerous requirement to be put off and procrastinated on, rather a source of strategic value and a useful planning tool.
This thinking is understandable, but it also creates an environment in which security is thought of as being at odds with agility, responsiveness, and growth. From the outside, these precautions appear to slow down operations and ultimately act as a stumbling block to operations. And, to be sure, there’s an element of that present in some of the solutions currently on the market. Web application firewalls, for instance, can be useful for filtering out malicious HTTP traffic, but they have a tendency to slow your website down, which can be detrimental to traffic and conversions. But not everything falls into this category—in fact, if you know where to look it’s possible to find solutions that will actually improve webpage performance via compression, bringing both security and the potential for increased conversions.
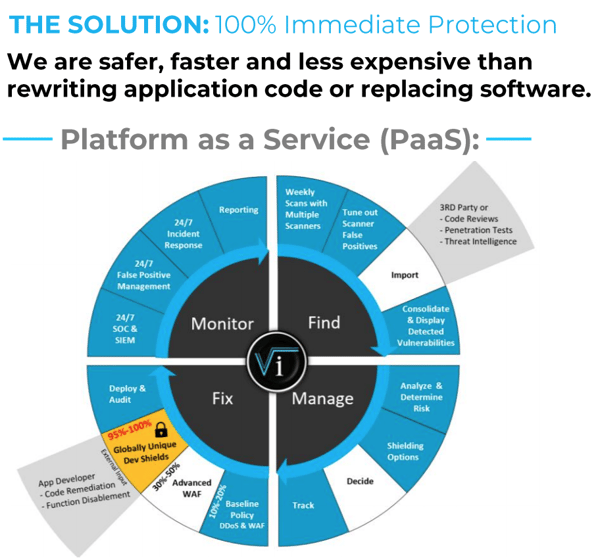
The Power of Application Shielding for Protecting Your Endpoints
We don’t want to leave you in suspense, so we’ll say upfront that AI-powered application shielding is one of the technologies we alluded to above with the power to improve website performance. This kind of technology takes the basic premise of a WAF (setting rules about web traffic in order to cover known vulnerabilities and weaknesses in your app) and improves upon it. How?
- Because shielding solutions of this kind can maintain an application state, they’re able to protect against a much wider array of known attacks than WAFs can.
- Not only that, but they can do so without creating a glut of false-positives (or false negatives, for that matter). Since these false-positives are among the reasons that WAFs can slow your system down, the increased accuracy with which the system creates rules for HTTP traffic can be a huge boon.
- Thus, for all of your known vulnerabilities, you could rely on the shielding technology to protect your systems at the relevant endpoints—without you or the shielding system having to touch a single line of code on your own servers.
This last facet of the shielding technology under discussion is particularly critical. Since the protections it offers effectively alleviates the pressure to remediate code (for legacy code that can’t be remediated, it even removes the pressure to modernize existing codebases), you’re able to keep your systems protected during what can often be drawn-out, months-long bug fixes. This isn’t just a matter of reduced time pressure—rather, it puts businesses in a position to take a more holistic, strategic view of their application’s codebase, and address different flaws or bugs in the way that makes the most business sense.
As you can imagine, having the freedom to do so can provide a number of real strategic advantages.

Strategic Advantages of Cyber Security
Okay, let’s say you’ve got a new product release scheduled for the middle of next month. You’ve aligned your offering with new and emerging market data—you’re as confident as can be that your new rollout will speak to your existing users, and it may even help you gain some new ones. Your developers have been hard at work, and as the release date approaches everyone’s feeling at least a little stress. From a strategic perspective, which position would you rather be in?
- In one scenario, you have very little formal cyber security infrastructure in place outside of your SecOps team. Once your DevOps has gotten their end of the new offering up and running, they hand it over to SecOps, who hopefully doesn’t find anything glaringly wrong. If they do find something, you run the very real risk that you’ll have to delay your release while you remediate, or ship a product that isn’t secure—basically a no-win situation.
- On the other hand, if cyber security is integrated into your infrastructure and your planning process, your DevOps teams can work with the confidence that any potential software issue can be shielded upon release and then remediated later. Here, instead of slowing down release schedules and putting up barriers, SecOps can take a strategic approach to code remediation and other security matters. They can even work hand in hand with DevOps throughout the development process to optimize your app from an InfoSec perspective.
In all likelihood, given the choice between the two options above, you’d say that the second one puts your business in the best strategic position. Not only are any potential vulnerabilities being covered by the shielding technology, but you’re in charge of your own release schedule—meaning that you can speed up time-to-market and decrease the potential for disruptions.
DevOps vs SecOps
Once you’re able to generate strategic plans with the knowledge that security lapses aren’t going to throw everything out of whack at the last second, you can obviously improve on any number of KPIs related to speed-to-market and OOE (overall operational efficiency). But that’s not all. You can leverage these tactical advantages into more cohesive and value additive processes overall. While the scenario we sketched out above where cyber security precautions were restricted and siloized essentially pitted SecOps and DevOps against one another, the alternate path gives you the power to integrate those processes. The result is that your development processes can become more security-conscious overall, and your security engineers can become a bigger part of the design and implementation process (since they’re no longer relegated to scrambling to find security flaws and prevent problematic releases).
In this way, you can begin to break down silos and build out processes that let your people do what they do best—for development teams, this means responding to customer problems and strategic initiatives in a flexible, responsive way; for security experts, this means offering guidance throughout the entire development process, in order to continually improve app performance. Crucially, these resources are now freed up to be used in whatever way best fits the current objectives. Rather than being beholden to long and complex remediation processes and hair-on-fire release schedules, you can take a long view that incorporates changing conditions and capacity needs. The best part is that all the while you’re covered when it comes to any and all known vulnerabilities.
How to Implement the Right Cyber Security Framework
Okay, we’ve seen the way that cyber security—far from being a drain on company resources or an unfortunate fact of life—can actually add value from a strategic planning perspective. It accomplishes this by offering you a modicum of planning certainty—there’s no reason to push back a release because of security concerns if you have a security solution that can cover those issues until there’s time to remediate—which you can then leverage into improved coordination across functions. The question is: how do you implement the right cyber security framework to make this a reality?
Like we alluded to above, automation is your friend here. AI-powered application shielding technology that can truly cover your endpoints and prevent known attacks is a good place to start. Because the goal here is to speed up operations, rather than letting things get bogged down, you’ll also want something that’s as close as possible to a turnkey installation. While most WAFs and other similar solutions require extensive and complex installation and maintenance (which can put you right back where you started), it is possible to find solutions for which that’s not the case. Often, those will involve some element of management on the part of a vendor. With that management in place, you can skip any sort of laborious installation and maintenance workflows and spend your time and resources on more value-additive tasks.
By combining endpoint protection with managed cyber security services in this way, you can completely rethink the role that security plays in your project management and product development processes. Over time, the impact of this added flexibility can multiply, putting you in a position to execute your strategic initiatives more effectively than ever before.
What many corporate decisionmakers fail to see when cyber security comes up is that, with the right solution, you don’t have to tie your ROI calculations to staving off data breaches and nothing else. On the contrary, the right solution can help you to improve your time-to-market, prevent disruptions related to legacy IT and difficult-to-remediate bugs, and create better alignment between different touchpoints in the development cycle. The only question is how to find the right solution to make those positive drivers of ROI possible.
1. Be Proactive
If you’re looking at this article and you haven’t just been subject to a data breach, you’re already doing a good job of being proactive. At the same time, you need to make sure to follow through. To figure out the features and elements your cyber security operations should have, you need to think about your company’s structure, its long- and short-term goals, and your vision of its transformation over time. In other words, you’ve got to plan for the business you want, not for the business you’ve got. If you wait until a catastrophic security incident, you’ll wind up scrambling to put a system in place that specifically addresses the new security flaws that you’ve just unwillingly discovered—meaning that in all likelihood you’ll be a taking reactive, potentially short-sighted approach to your selection process. Sure, any cyber security deployment should be accompanied by some degree of urgency, but if you can sit down to define your needs in a moment where that urgency is at a minimum, you’ll have a much easier time taking the long view and prioritizing long-term ROI.
2. Assess Your Threat Model
As we get through our suggestions on this list, we’ll make a point of highlighting the areas where the right cyber security solution can actually add strategic value for your operation. Before we dig into those areas more fully, however, we do need to talk about threat models and attack surfaces. Ask yourself:
- What is the general risk model for cyber security in your industry? If you’re in banking, for instance, you’ll need to think about things like wire fraud and SWIFT fraud; for healthcare, you might be more concerned with ransomware or DDoS attacks.
- What does your current IT environment look like? Is your company using legacy applications that have the potential to increase your overall security risk?
- What does the remediation process look like at your company? When you find a security vulnerability, how long does it take to cover and/or resolve the issue?
- How well are your personnel trained on web application security issues? Are your employees likely to be taken in by phishing emails? Do your developers consider security when writing code for your various applications?
The answers to these questions should tell you a lot about what kinds of attacks you’ll need to defend against and what sorts of systems you might need to put in place. This is an area where it might even be useful to talk to an outside consultant who can give a clear-eyed assessment both of how prepared you are to stave off cyber attacks and how well security is integrated with other workflows.
3. Create Alignment Between Cyber Security and Other Initiatives
Speaking of integrating security with other workflows: once you have a handle on your threat model, it’s time to think beyond merely preventing attacks and consider the ways in which your cyber security solution can add value to your other business areas. This, too, will depend on the answers to the questions you gave above. For instance, if you’re working with a lot of legacy IT, you could look out for solutions that can cover the security flaws in these systems without forcing you to replace them. In this way, you can align your long-term IT goals with your immediate security concerns. By the same token, if you have a big product release on the horizon and you’re concerned about resource usage, you should look for solutions that increase your overall amount of freedom: this might take the form of application shielding capabilities that protect your system from known vulnerabilities so that you don't have to scramble to remediate, a managed service that frees up your resources for more valuable tasks, or even a combination of the two.
Again, you’ll need to take stock of what’s happening within your enterprise: What are your top strategic goals for the next year, two years, five years, etc.? What are the top causes of delay that you’ve been encountering as you try to release new applications or update old ones? If security concerns are delaying your time-to-market or hampering your developers, you’ll want to adopt a solution that can integrate seamlessly into existing workflows to support your DevOps team. By the same token, if you’re hoping to create an integrated DevSecOps team to drive smarter development projects, something that frees up your resources while covering known security vulnerabilities is an absolute must.
4. Gauge Your In-house Capabilities
In the section above, you may have noticed that we brought up the possibility of implementing a managed cyber security solution, rather than trying to manage everything in-house. That’s not just idle talk—on the contrary, for businesses that don’t have robust security operations of their own, or who don’t want to utilize their person-power on security software maintenance (web application firewalls, for instance, are notoriously fiddly to set up and maintain), a managed service can be an excellent way to create the exact sort of strategic alignment that we discussed above. And, of course, most businesses are fairly likely to fall into “insufficient internal resources” camp when it comes to robust cyber security operations. To wit, a recent study found that only 30-40% of companies (depending on size) actually had a security operations center. If you’re part of that 30-40%, a managed service might be redundant, and you might be better off seeking out a solution that you can manage on your end.
For the other two-thirds of businesses, you’ll have to consider how easy or difficult it would be to ramp up to a point where you could handle all of your security needs in-house. The list of competencies you’ll need to cover in this department can cover any number of things:
- Incident response/detection
- Penetration testing
- Security audits
- Security training and education
- Remediation for vulnerabilities
- Solution maintenance
On top of this, you’ll need to retain a responsive posture by keeping up-to-date on all the latest CVEs, staying current on threat models and technology, and reevaluating your own technologies and best practices so that they don’t go out of date. Frankly, this is an area where an outside partner whose sole focus is cyber security can be helpful even if you already have an SOC. In this way, you can augment your own capabilities to maintain real-time protection.
Of course, you could take the time and effort to hire, onboard, and train new personnel in order to develop those capabilities and keep them current—whether that’s immediately or in the long-term. At the same time, talent is often hard to come by these days, and once you’ve developed strong security expertise it can become difficult to scale up or down as your needs change.
Whatever route you’re interested in, you’ll need to determine:
- What your current cyber security capabilities are;
- How those capabilities align with your other corporate goals;
- What level of capacity and competency you’d like to have in-house;
- What steps you would have to take to get from where you are now to where you’d like; to be, and how cost effective that process will be in short-, medium-, and long-term.
One you’ve gone through this exercise, you might be surprised to find that you’d actually be better off devoting your existing security resources to collaboration across different functions.
5. Identify Quick Wins
No matter what approach you take when it actually comes to choosing a solution, getting buy-in from other stakeholders is going to be a key part of the process. Whether you’re trying to get your CFO on board with the costs of a managed service or you’re trying to convince your CISO that you can actually improve security overall by giving SecOps the leeway to act as more of a collaborator with your other developers, you’ll want have some way of immediately displaying value and giving others an idea of how your cyber security solution can help the business going forward. This might be as simple as demonstrating how much time you can save by ditching your WAF and utilizing an application shielding solution instead. Or, it might mean demonstrating the savings in time and resources you can effect by covering the known vulnerabilities in your legacy applications. Or you might choose a solution that condenses HTTP traffic in such a way that immediately speeds up your web apps.
Whatever quick wins you’re able to find, make sure they, too, mesh with your larger strategies. In this way, you can establish your cyber security practices as a tool for meeting longer-term goals, rather than an expensive albatross that slows down your development cycles. Once you’ve clearly demonstrated this fact to other key stakeholders, getting more sustained buy-in for your cyber security implementation will be a breeze. Instead of slow and grudging acceptance of changes that seem like a hassle, you can drum up real enthusiasm for a time- and labor-saving solution.
Learn More About Intertec’s Managed Cyber Security Services
Intertec provides cutting-edge managed cyber security services based on sophisticated application shielding technology—helping global businesses to cut down on code remediation costs while preventing data breaches. Click here to learn more. Prefer a personal consultation? Go ahead and schedule a meeting with us here!